
With confirmation from the US Government as well as Cisco Talos, the Chinese state-sponsored threat actor nicknamed Salt Typhoon Group is said to have carried out an intrusive campaign against Telecom Networks in the US.
As reported by The Wall Street Journal last year, cyberattacks were launched against US telecommunication companies such as AT&T and Verizon. However, it wasn’t until this year the US CISA confirmed the attack to be part of the Salt Typhoon campaign. This was followed by Cisco Talos’ confirmation who says in their blog post that “the threat actor was able to gain access to core networking infrastructures,” and described the activities they observed as well as provided detection and preventative measures.
At the heart of the intrusion lies a custom malware named ‘JumbledPath.’ According to Cisco, this malware is engineered with sophisticated evasion techniques – dynamic code obfuscation and encrypted command-and-control-communications – to stealthily move within telecom networks.
The malware’s modular design not only helps maintain continuous access, but it also facilitates the covert transfer of sensitive data, which highlights the threat actor’s tailored approach and high level of operational sophistication.
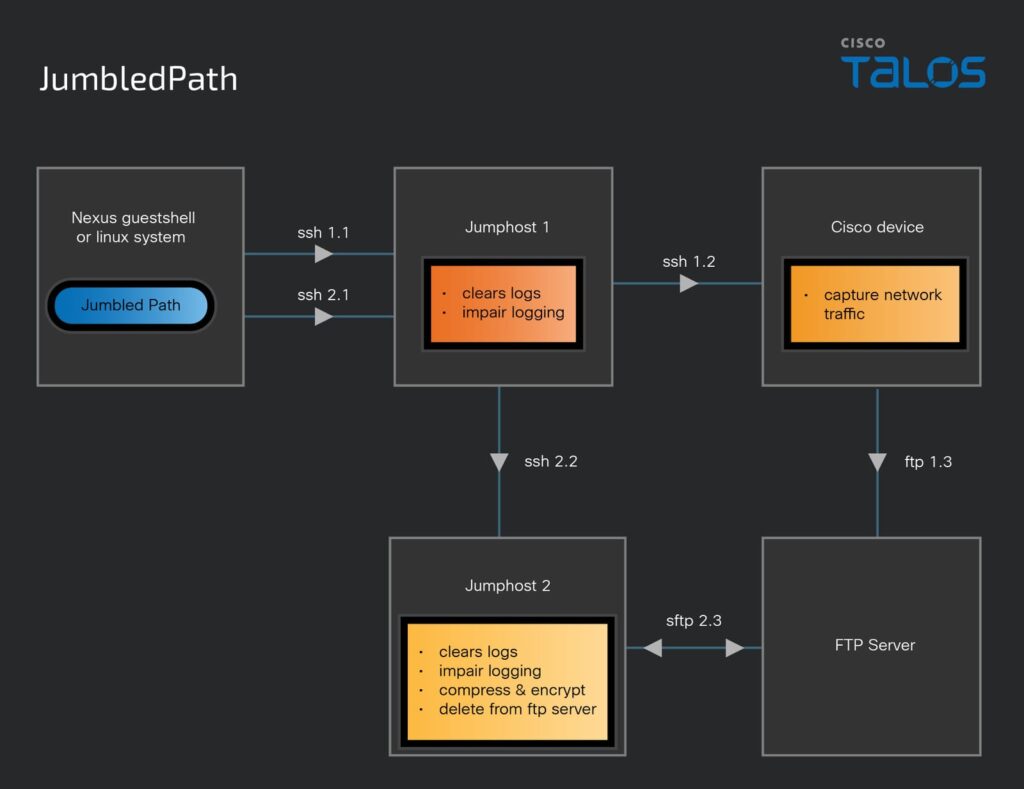
The diagram above from Cisco Talos illustrates how the hackers, using JumbledPath installed on a Linux-based system, moved through different systems to steal network data while covering their tracks. From there, they accessed different servers (jump hosts) and a Cisco device using secure shell (SSH) connections. The Cisco device was used to capture network traffic, meaning they could monitor and steal data moving through telecom networks.
To stay hidden, the hackers cleared logs and disabled tracking at each stage, ensuring that their activities remained undetected. Finally, they compressed and encrypted the stolen data before sending it to an FTP server which made it harder for investigators to trace.
In response to public reports indicating that the threat actor was able to gain access to core networking infrastructure, Cisco says, “there was only one case in which we found evidence suggesting that a Cisco vulnerability (CVE-2018-0171) was likely abused. In all the other incidents we have investigated to date, the initial access to Cisco devices was determined to be gained through the threat actor obtaining legitimate victim login credentials.”
Cisco also adds that, “A hallmark of this (Salt Typhoon) campaign is the use of living-off-the-land (LOTL) techniques on network devices. It is important to note that while the telecommunications industry is the primary victim, the advice contained herein is relevant to, and should be considered by, all infrastructure defenders.”
The Chinese-state sponsored threat actor has also been involved in operations that the US government agencies have referenced under the name of “The Volt Typhoon.” While Salt Typhoon is primarily known for its attacks on US telecommunication networks using tools like the JumbledPath malware, the broader Volt Typhoon campaign – as noted in a CISA report – seems to be involved in a range of targets across critical infrastructure sectors in Communications, Energy, Transportation Systems, Water and Wastewater systems.
However, the exact relationship between the two campaigns and the full scope of Volt Typhoon’s activities remain subjects of ongoing analysis, even as the US continues to fight an escalating cyber-warfare from China.
It is crucial to note that attacks like this weaken national security strength and posture, as well as raise concerns about the exploitation of recent vulnerabilities for strategic advantage in the international political system, given that telecommunication networks are important to government agencies, for defense operations, and for emergency response systems.
It is applaudable that US agencies such as the CISA (Cybersecurity Infrastructure Security Agency) and the NSA (National Security Agency) have stepped their cybersecurity efforts up, where they are now working closely with private-sector companies to strengthen authentication protocols, monitor for suspicious activities, and fix known vulnerabilities.

